Antivirus Vendors React To The CIA 'Vault 7' Leaks

Last week’s CIA leaks from WikiLeaks revealed that most antivirus programs may have been bypassed at one point or another by the CIA. We’ve asked the antivirus companies about their opinions on the leaks and what they intend to do next.
Most Antivirus Tools Vulnerable To CIA Attacks
According to WikiLeaks’ leaked documents, most popular antivirus tools have been bypassed and exploited by the CIA. This fact alone isn’t as surprising as one may initially think, because it’s actually quite common for sophisticated attackers to be able to bypass most popular antivirus programs. That’s how they deliver their malware in the first place.
The real problem may come from the fact that antivirus programs in general aren’t as secure as you might expect them to be. Also, because of their deep hooks into the operating system or browsers, they can sometimes make users even more vulnerable to attacks (at least of the more sophisticated type).
Although 21 antivirus and security solutions vendors were included in a WikiLeaks document describing bypasses against them, WikiLeaks left information about the attacks on only three antivirus vendors: F-Secure, Avira, and AVG (recently purchased by Avast, another antivirus vendor). The organization said it didn’t want to expose information that might endanger actual CIA operations, which may be why the information on most of the others was redacted.
F-Secure
The CIA had the following comment on F-Secure’s antivirus software, implying that F-Secure isn’t all that secure, and that it can be bypassed easily:
In OSB's experience, F-Secure has generally been a lower tier product that causes us minimal difficulty. The only annoyance we have observed is that F-Secure has an apparent entropy-based heuristic that flags Trojaned applications or other binaries containing encrypted/compressed payloads. Two defeats are known to exist: On involves using RAR file string tables in the resource section, the other involves cloning a RAR file manifest file – the manifest technique also works against Avira's entropy-based heuristics.
We asked F-Secure’s Chief Research Officer (CRO), Mikko Hyppönen, what he thought about the CIA’s comment, and this was his reply:
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Well, we don't mind being the "annoying troublemaker," as we are characterised in the leaks. The leaks detail a large amount evasions for basically all the end-point security products.I think it's a fair game. CIA has targets they are trying to get to, and some of those are protected by products like these. CIA wouldn't be doing their job if they wouldn't be developing techniques like these.We don't consider this to be a vulnerability as such, as they are not crashing us or exploiting us. Anti-virus products are never perfect; some attacks will always succeed. A superpower intelligence agency with massive budgets can definitely do that.I much prefer them doing it like this, instead of trying to twist our arm to let them through.
It’s not clear how the CIA could force a backdoor on F-Secure, because the company has an advantage compared to some other antivirus products in that it’s based in Finland. The company does have two offices open in the U.S., too, but presumably that still limits the extent to which the U.S. government could force a backdoor into its software.
Avira
The CIA doesn’t seem to have a great opinion about Avira either, calling it "easy to evade":
Avira has historically been a popular product among CT targets, but is typically easy to evade. Similar to F-Secure, Avira has an apparent entropy-based heuristic that flags binaries containing encrypted/compressed payloads, but there are two known defeats.
Avira released a statement to Tom’s Hardware in which it said that the issue was minor and was fixed a few hours after WikiLeaks released the CIA “Vault 7” documents. It also said that the exploit described in the CIA document affected only a subset of the rules of one of Avira’s several different and independent detection modules.
The company mentioned that it did not see any malware samples in its database that used the described bypass, implying that the CIA may have not used the bypass against any of its users. However, because WikiLeaks redacted some of the information, we don’t know whether the CIA used other techniques to hide its bypass in ways that Avira couldn’t detect.
The antivirus company added that it will continue to develop new detection features and protection layers to avoid similar bypasses in the future.
AVG (Avast)
In the leaked document, the CIA seemed to say that AVG does catch the agency’s payload, but only well after its execution--and of course by then, it’s too late. That means the CIA could have chained together multiple exploits to disable the antivirus software before it could react.
AVG catches a payload dropped to disk and launched via link file well after execution (process hollowing).
In an email reply to Tom’s Hardware, Avast’s Ondrej Vlcek, CTO and GM of the company’s consumer division, said that the issue wasn’t critical, because it would be too difficult to tie together multiple exploits that could both penetrate the system’s defenses and disable the antivirus software.
However, some of the more sophisticated attacks do use multiple exploits, because they have to bypass multiple defenses on a user’s system, so it’s not that uncommon. Operating system defenses have gotten much better in the past decade, so it’s not as easy to infect someone with malware with a single exploit, especially if the target is more technically inclined and has taken the proper precautions. Either way, AVG’s parent company, Avast, is now saying that this particular issue shouldn’t exist anymore in the AVG antivirus.
Comodo
In a different document, the CIA lauded the older Comodo 5.x architecture for being almost impenetrable due to how paranoid it was about any and all system processes, but then took it all back when it said the following Comodo 6.x architecture was much more exploitable due to the fact that it was clearing all system processes. The CIA said in the document that this would allow an attacker to easily bypass the Comodo firewall with a kernel exploit:
Comodo, as you may know, is a colossal pain in the posterior. It literally catches everything until you tell it not to, including standard windows services (say what?!?)....at least, that's what happens on Comodo 5.X. In 6.X, Comodo apparently decided that catching things that were part of windows was a Bad Thing(tm). Their "fix" was... kinda lame.Anything running as SYSTEM is automatically legit under 6.X. ANYTHING. Let that sink in. Got a kernal [sic] level exploit? Good, because you can drop the kitchen sink and the contents of your garage and as long as you continue to run as SYSTEM you are golden. Yeah.Needless to say, Comodo 6.X doesn't catch nearly as much stuff. Comodo's user base, paranoid bastards that they are, has apparently caught wind of this and lots of them haven't upgraded to 6.X. Kind of a shame, cuz [sic] this is a hole you could drive a very large wheeled freight carrying vehicle through. However, if you're lucky enough to be going against a target running 6.X, have fun!
Unlike most of the other antivirus makers, Comodo seems to have received somewhat a of backhanded compliment, which the company has taken it as a full compliment:
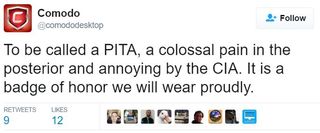
Comodo said that version 10 of the Comodo firewall was released earlier this year, and it shouldn’t be vulnerable to such attacks anymore. That will remain to be seen.
No Backdoors Reported (Yet)
As the attacks revealed by WikiLeaks are already a few years old, we don’t know what other antivirus-bypassing capabilities the CIA may have. Therefore, even if the revealed issue were fixed, there may be others that the antivirus companies haven’t found yet.
However, as F-Secure’s Hyppönen also said, the silver lining from the CIA documents showing that the agency can bypass most antivirus tools is that the agency still has to break them just like any other attacker.
From the unredacted documents that have been released so far, there doesn’t seem to be any evidence that the antivirus companies were working with intelligence agencies to undermine their customers’ security. That may be a sign (and a good one) that at least the antivirus vendors are working in their customers' interests, even if sometimes that's not enough to stop more sophisticated attackers such as the CIA.
-
Sharky36566666 All the AV vendors have no choice but to spin this revealing leak of how easily the majority are bypassed to some extent. The CIA reports are a direct condemnation of their products value proposition as promoted in the marketing materials. For them to point out the "good" parts about their products within the CIA reports which is a document explaining how to they are all exploitable is the definition of a pollyanna.Reply -
Math Geek these are internal memos and not official public records. big difference. this is how people talk to one another so it's not exactly odd that informal internal memos would reflect that.Reply
only stuff that is for public consumption gets the royal treatment of pr guys making sure it's a full on dog and pony show. no time for that in day to day operations :) you'd be surprised how candid meetings and such are when no one is watching. think even trump would be stupid enough to say what he did about "grabbing women by the *****" if he knew the public would be listening?? not even he is that stupid to "officially" say such things. -
turkey3_scratch ReplyComodo's user base, paranoid bastards that they are
Wow CIA, very mature, professional write-ups you got here. -
ddelrio Amusing that they called Comodo users "paranoid", when, in fact, it sounds like the precautions they took were valid.Reply -
koss64 I agree with the CEO of Fsecure Mikko Hyppönen who said that its not the world collapsing in on itself,its going to happen,if law enforcement cant knock on your door if they want you they are going to make their own way in your house. Its better they do this than make a public spectacle of making a backdoor.But still all this is from Wikileaks so I take all of it with a artery clogging dose of salt :(Reply
BTW Mr.Armasu, I genuinely thank you for not injecting a lot of your opinions in this news article, I found it a pleasant and informative read. -
Math Geek i do agree that i don't mind the cia hacking in. that's the way the game is supposed to be played. i don't like when they try to mandate the backdoors into place.Reply
but if they put the effort in and get in themselves, well not much we can do about it that. -
poochiepiano Reply19428894 said:these are internal memos and not official public records. big difference. this is how people talk to one another so it's not exactly odd that informal internal memos would reflect that.
only stuff that is for public consumption gets the royal treatment of pr guys making sure it's a full on dog and pony show. no time for that in day to day operations :) you'd be surprised how candid meetings and such are when no one is watching. think even trump would be stupid enough to say what he did about "grabbing women by the *****" if he knew the public would be listening?? not even he is that stupid to "officially" say such things.
Yeah, I figured it was internal stuff, but even within my company, internal e-mails and communications usually contain relatively professional language.
Most Popular







